
Researcher says they were behind iPhone popups at Def Con
Several attendees at the hacking conference Def Con reported seeing mysterious and persistent pop ups prompting them to use their Apple ID to connect to an Apple TV, or to share a password with an Apple TV nearby, according to attendee tweets over the weekend and people who spoke to TechCrunch.
These incidents confused and dumbfounded some of the attendees, who weren’t sure how these alerts — for lack of a better word — were carried out, or what the goal was. Hacker shenanigans during Def Con are a decades-long tradition, and are more often pranks than actual malicious attacks.
In this case, it may have just been a research project.
On Saturday, a security researcher who goes by Jae Bochs said on Mastodon that it was them who was behind these activities.
“I’ll come clean: it me,” Bochs wrote.
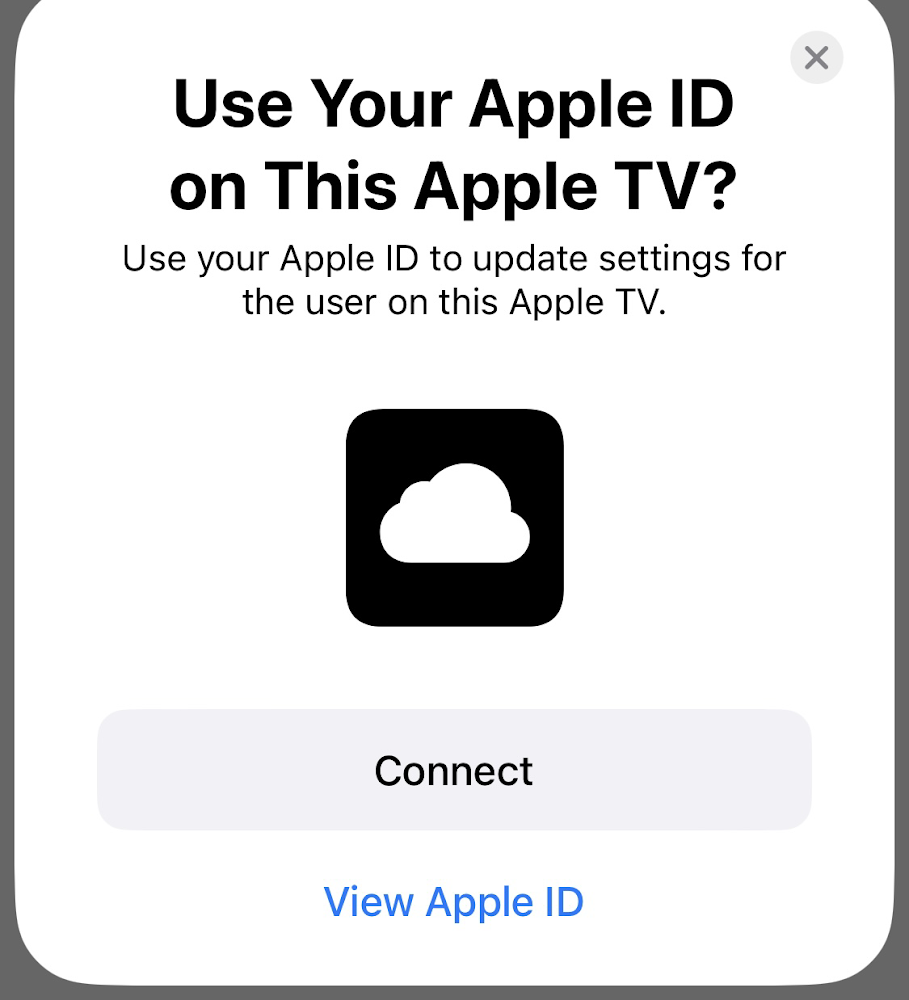
Bochs said the alerts they sent out were built with two purposes: to remind people to “really shut off Bluetooth,” and not just from the Control Center, and “to have a laugh.”
Bochs said that this experiment wasn’t designed to collect any data, but rather to send Bluetooth “advertisement packets that don’t require pairing (and as such aren’t stopped by the control center toggle).”
It’s unclear, however, if they — or someone else researching this feature — could have actually collected data and done something more malicious.
The researcher said that to stop these pop ups someone needs to turn off Bluetooth via the Settings app, not from the Control Center, which users can invoke by swiping down from the top right corner of the iPhone.
TechCrunch spoke to eight attendees who said they saw one or both of the prompts while at the conference. Some of them saw the pop ups several times over the weekend, and at different places around the conference floor.
Opinions on the merits of this research project, which was not publicized in advance, varied.
“I think it’s hilarious. It was annoying as hell but also reminded me that control center is bad 😂,” said NinjaLikesCheez, an iOS application security researcher who saw the pop ups.
Dan Guido, the CEO of security research firm Trail of Bits, wasn’t amused.
“I think he abused a bunch of users when he should take his complaints to Apple,” Guido told TechCrunch.
In response to someone who praised the experiment as “some OG #DEFCON shenanigans,” Bochs wrote that was the “vibe” they were hoping for.
“Glad I could add a little harmless WTF to everyone’s day,” they wrote on Mastodon.
The common denominator, at least for the people who spoke to TechCrunch, is that none of them had turned on Lockdown Mode, a special iPhone feature that limits some functionalities with the goal of reducing the risk of getting hacked. This reporter was using Lockdown Mode and never saw either of these prompts.
Bochs said they were hoping to submit a talk based on this experiment, and to “have it working” with the upcoming iOS 17 feature called “NameDrop.” This new feature will allow iPhone owners to share their contact with someone else with an iPhone or Apple Watch by simply bringing the phones close to each other.
Apple did not respond to a request for comment.
When asked whether the conference organizers had seen these pop ups themselves or whether they had been reported to them by attendees, Def Con spokesperson Melanie Ensign simply sent a link to Bochs’ Mastodon post.
Do you have information about these alerts and how this iPhone feature works and whether it can be abused for a malicious attack? We’d love to hear from you. From a non-work device, you can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, or via Telegram and Wire @lorenzofb, or email lorenzo@techcrunch.com. You also can contact TechCrunch via SecureDrop.


