
LetMeSpy, a phone tracking app spying on thousands, says it was hacked
A hacker has stolen the messages, call logs and locations intercepted by a widely used phone monitoring app called LetMeSpy, according to the company that makes the spyware.
The phone monitoring app, which is used to spy on thousands of people using Android phones around the world, said in a notice on its login page that on June 21, “a security incident occurred involving obtaining unauthorized access to the data of website users.”
“As a result of the attack, the criminals gained access to e-mail addresses, telephone numbers and the content of messages collected on accounts,” the notice read.
LetMeSpy is a type of phone monitoring app that is marketed for parental control or employee monitoring. The app is also specifically designed to stay hidden on a phone’s home screen, making it difficult to detect and remove. Also known as stalkerware or spouseware, these kinds of phone monitoring apps are often planted by someone — such as spouses or domestic partners — with physical access to a person’s phone, without their consent or knowledge.
Once planted, LetMeSpy silently uploads the phone’s text messages, call logs, and precise location data to its servers, allowing the person who planted the app to track the person in real-time.
For their deep level of access to a person’s phone, these surveillance apps are notoriously buggy and known for rudimentary security mistakes, with countless spyware apps over the years getting hacked, or leaking, and exposing the private phone data stolen from unwitting victims.
LetMeSpy is not much different.
Polish security research blog Niebezpiecznik first reported the breach. When Niebezpiecznik contacted the spyware maker for comment, the hacker reportedly responded instead, claiming to have seized wide access to the spyware maker’s domain.
It’s not clear who is behind the LetMeSpy hack or their motives. The hacker intimated that they deleted LetMeSpy’s databases stored on the server. A copy of the hacked database also appeared online later the same day.
DDoSecrets, a nonprofit transparency collective that indexes leaked datasets in the public interest, obtained a copy of the hacked LetMeSpy data and shared it with TechCrunch. DDoSecrets said it was limiting the distribution of the data to journalists and researchers, given the amount of personally identifiable information in the cache.
TechCrunch reviewed the leaked data, which included years of victims’ call logs and text messages dating back to 2013.
The database we reviewed contained current records on at least 13,000 compromised devices, though some of the devices shared little to no data with LetMeSpy. (LetMeSpy claims to delete data after two months of account inactivity.)
In January, LetMeSpy’s website said its spyware was used to track over 236,000 devices and collected tens of millions of call logs, text messages, and location data points to date. At the time of writing, the site’s counters read as zero. Much of the site’s functionality also appears to be broken, including the spyware app itself. TechCrunch analyzed the LetMeSpy phone app’s network traffic, which showed that the app appeared to be non-functioning at the time of writing.
The database also contained over 13,400 location data points for several thousand victims. Most of the location data points are centered over population hotspots, suggesting the majority of victims are located in the United States, India, and Western Africa.
The data also contained the spyware’s master database, including information about 26,000 customers who used the spyware for free and the email addresses of customers who bought paying subscriptions.
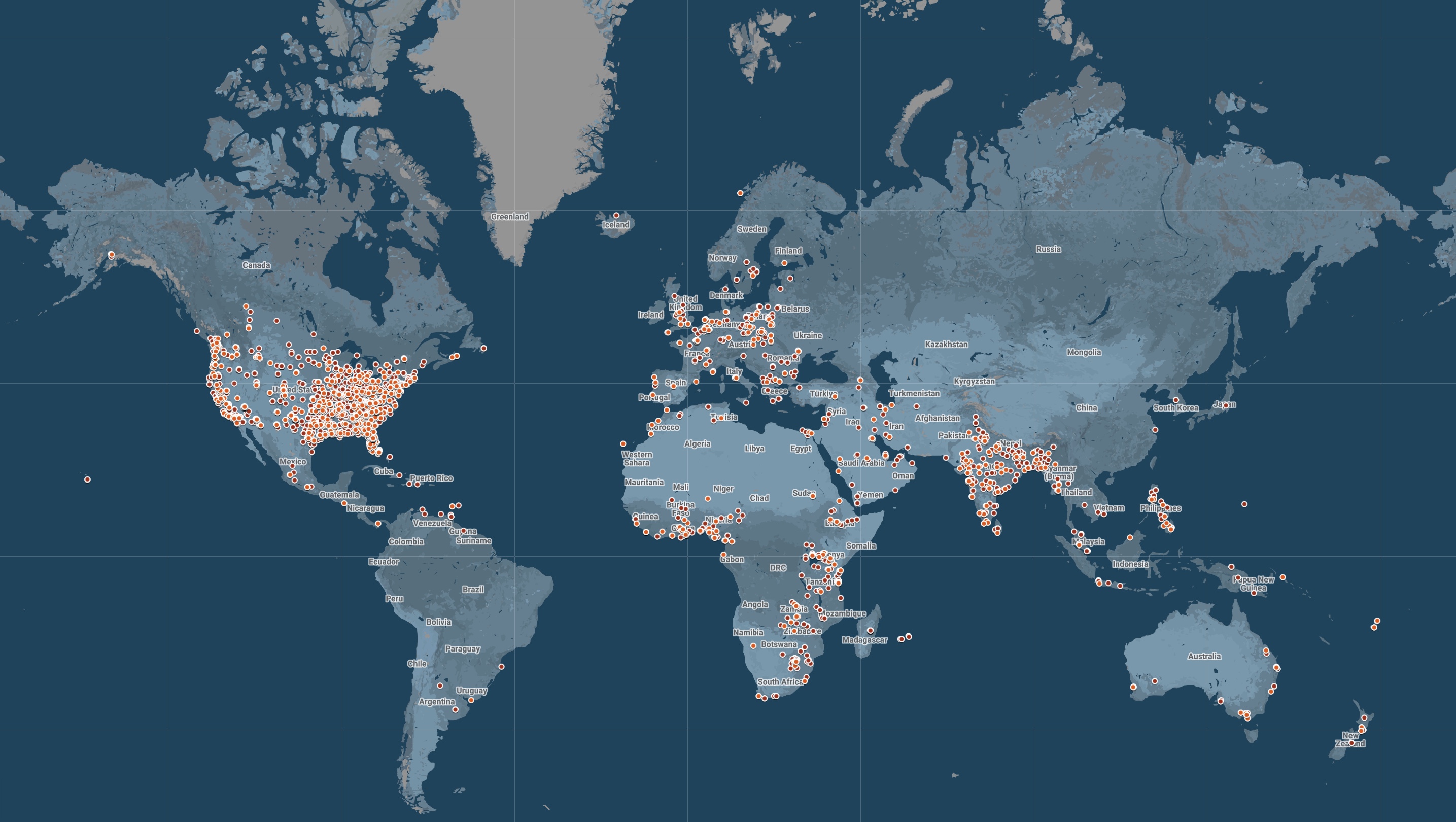
A world map showing the victims’ location data points in clusters around the U.S., India and parts of Africa. Image Credits: TechCrunch
It’s not uncommon for spyware makers, including LetMeSpy, to keep the real-world identities of its developers away from public view, often as a way to shield themselves from the reputational and legal risks that come with facilitating large-scale covert phone surveillance, which is considered a crime in many countries.
But information in the leaked database shows LetMeSpy is built and maintained by a Polish developer called Rafal Lidwin, based in Krakow. Lidwin did not respond to multiple requests for comment.
LetMeSpy said in its breach notice that it had notified law enforcement and the Polish data protection authority, UODO, which did not respond to TechCrunch’s request for comment.
It’s unclear if LetMeSpy will notify the victims whose phones were compromised and spied on, or even if the company has the ability to do so.
Where in the past it’s been possible for victims to check for themselves if their data was compromised, the leaked LetMeSpy data contains no identifiable information that could be used to notify victims directly. Even if there was, notifying victims of spyware is tricky because it could also alert the person who planted the spyware and create an unsafe situation.
Android spyware apps are typically disguised to look like important system apps. LetMeSpy is easier to find and uninstall. The app is named “LMS,” and has a distinctive icon. We have a general guide that can help you remove Android spyware — if it’s safe to do so.
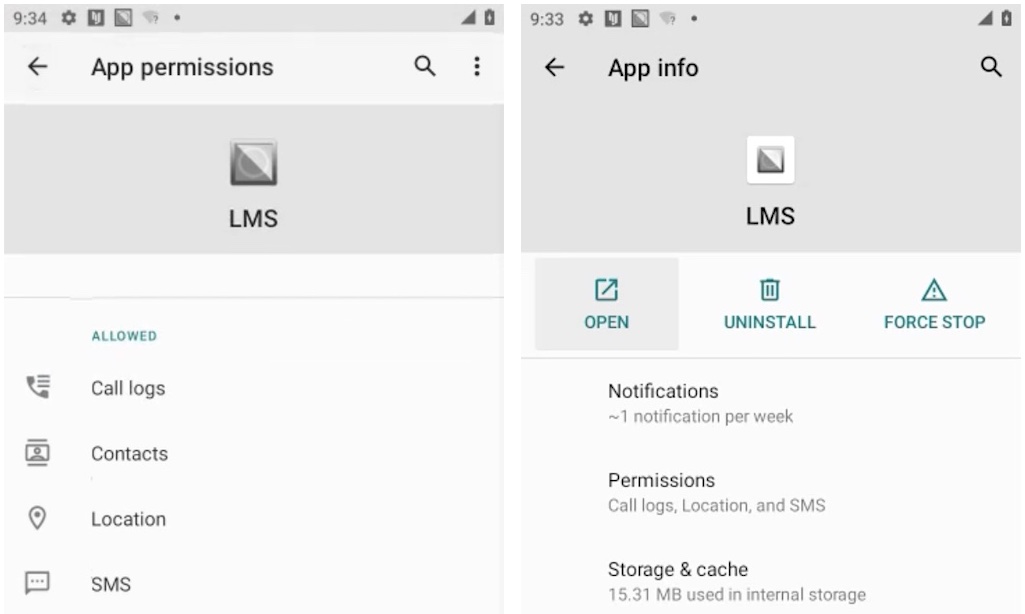
Side-by-side screenshots of the LetMeSpy app in Android. Image Credits: TechCrunch
You should also switch on Google Play Protect, one of the best safeguards to defend against malicious Android apps, if it isn’t already. You can do this from the settings menu in Google Play.
LetMeSpy is the latest in a long list of spyware and phone monitoring apps that have been hacked, breached, or exposed victim’s data in recent years: Xnspy, KidsGuard and TheTruthSpy, PhoneSpector, and Support King, to name a few.
If you or someone you know needs help, the National Domestic Violence Hotline (1-800-799-7233) provides 24/7 free, confidential support to victims of domestic abuse and violence. If you are in an emergency situation, call 911. The Coalition Against Stalkerware also has resources if you think your phone has been compromised by spyware. You can contact this reporter on Signal and WhatsApp at +1 646-755-8849 or zack.whittaker@techcrunch.com by email.
Read more:


