
Google’s Gradient backs YC alum Infisical to solve secret sprawl
Secret sprawl, where companies store authentication credentials and similar sensitive data across multiple locations, is a real and growing problem for any company wanting to avert a security breach.
Companies might have hundreds of secrets — such as API keys, passwords, or database access tokens — spread across their infrastructure, making it difficult to keep tabs on what is stored where, who has access to it, and whether any of this data has inadvertently found its way into the public realm. By way of example, back in 2017, Uber revealed a major breach that exposed the personal data of some 57 million customers, and while there were many security failures at play, the root cause stemmed from hackers that found an AWS access key in a GitHub repository of an Uber developer.
And it’s against that backdrop that we’ve seen a slew of startups and Big Tech tools go to market designed to help companies manage their secret sprawl. The latest is a San Francisco-based company called Infisical, which today announced it has raised $2.8 million in a seed round of funding led by Google’s Gradient Ventures to help companies of all sizes centralize their secret management.
Top secret
Infisical is pitching itself as a holistic secret-management platform combining all the components a company needs — a bit like what Rippling has been doing in the workforce management space, except for secrets, according to Infisical co-founder Vlad Matsiiako.
“As companies are becoming more digital and integrated with other software, it’s harder to manage all of their application and developer secrets — they have to buy multiple tools and give all of them access to their secrets, which is a security concern on its own,” Matsiiako explained to TechCrunch. “You can think of Infisical as an all-in-one secret management stack that combines all related product verticals for a company.”
This includes a dashboard for managing secrets across different projects and environments; client SDKs; a command line interface (CLI); native integrations with the likes of GitHub, Netlify, and Vercel; secret versioning and ‘point-in-time recovery’; audit logs; and secret scanning.
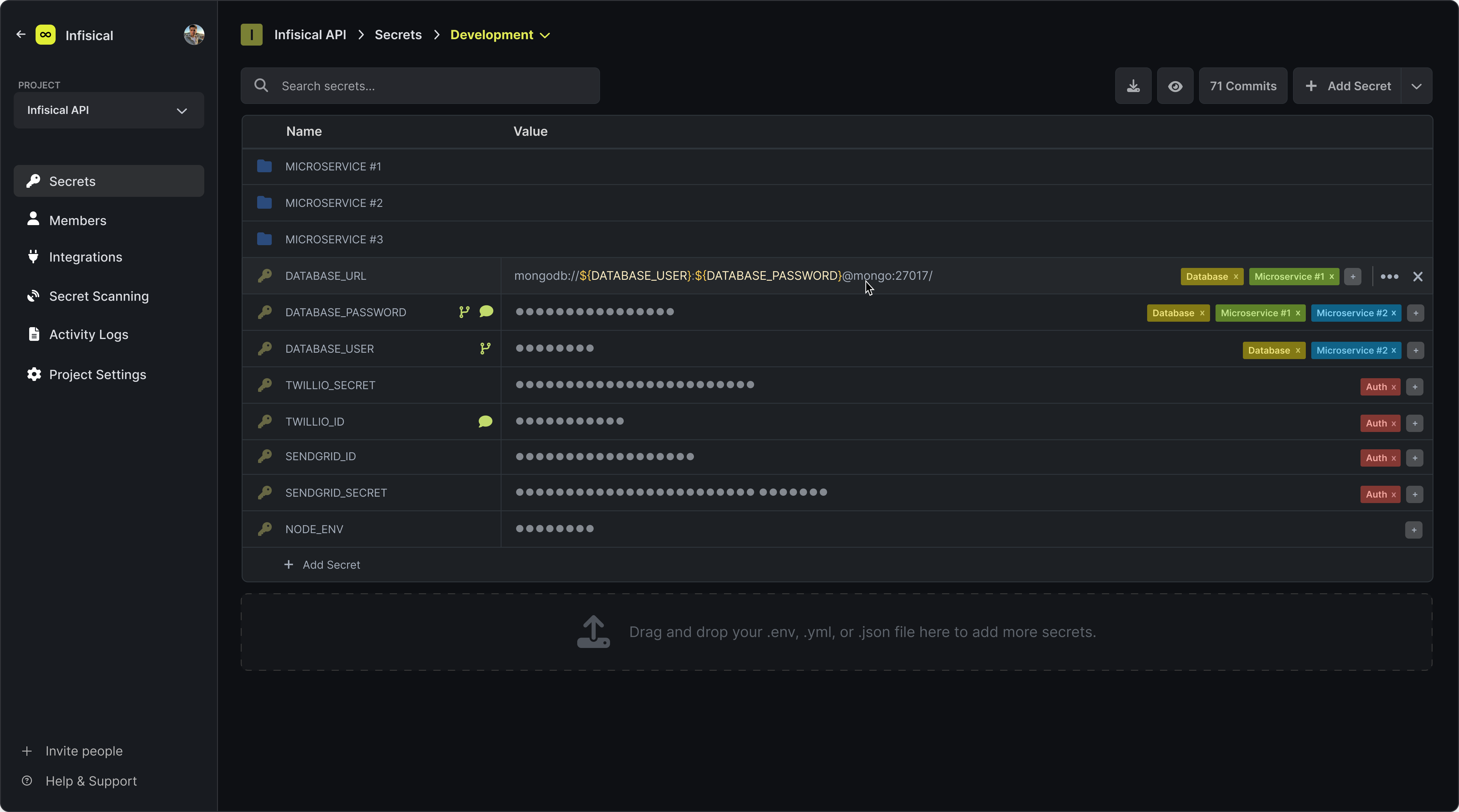
Infisical dashboard Image Credits: Infisical
As for business model, Infisical attracts revenue through its hosted cloud incarnation, which it sells as a SaaS, and through its self-hosted counterpart by selling enterprise-grade features.
The (sort of) open source factor
While Infisical is pushing itself as an “open source” SecretOps platform, a quick peek at its licensing on GitHub reveals that it’s perhaps more aligned with the open-core or source available realm, than it is the pure open source sphere. That is to say, while much of the platform’s core functionality is apparently available to use under the permissive MIT license, including secret-scanning and infrastructure integrations, it has retained a lot of the features — such as audit logs, single-sign on, recovery, and access controls — under a proprietary license under a separate enterprise edition (EE).
“Our entire codebase is available for everyone to view on GitHub, and we keep all core secret management functionalities available under the MIT license,” Matsiiako said. “We strongly believe that solo developers and hobbyists should be able to experiment with most features for free using either Infisical Cloud or Infisical self-hosted.”
The thinking here is that when users start considering Infisical in terms of deploying for critical commercial use-cases, they need more features such as advanced security and compliance. So even if a company has chosen to self-host Infisical, they still have to purchase an enterprise license to leverage core proprietary features.
“The goal is really to charge only larger enterprises,” Matsiiako added.
There are a bunch of similar tools on the market already, including the open source Vault project from billion-dollar cloud infrastructure giant HashiCorp, which has pretty much set the standard for the secret-management sector. However, Matsiiako argues that Infisical is aimed more at general developers rather than platform-engineering teams, making it easier to deploy with a flatter learning curve.
“Vault is difficult to adopt for developers without a background in security or infrastructure, and we find it to be more popular amongst security and platform-engineering teams,” he said. “Because of that, companies experience slower development cycles and some even resort to developing fully custom developer-facing solutions on top of — or instead of — Vault.
Other notable alternatives include Doppler and Akeyless, which are substantively proprietary SaaS products, and even tangential products such as secret-scanning tools from the likes of Gitguardian, a feature that Infisical is already supporting as part of its platform.
“By integrating secret scanning inside of Infisical’s bundle offering, we extract synergies between secret management and secret scanning, and a company looking for related secret management solutions now only needs to go through one vendor instead of multiple,” Matsiiako said.
The story so far
The company’s trio of founders — Matsiiako, Maidul Islam, and Tony Dang — met at Cornell University where they studied a mix of computer and data science subjects, going on to work at various companies such as AWS, Figma, and Bung. They then met up to kickstart their new venture together out of San Francisco last August.
“Throughout our past collective experiences and talking to industry peers, we recognized that managing application secrets was cumbersome and that problems in the secret management industry were far from being solved,” Matsiiako said. “It became clear to us that we needed to build an open-source solution that’s simple to use for secret management; being open source gives developers the flexibility of using Infisical Cloud or self-hosting it on their own infrastructure which is what larger companies frequently do.”
Infisical went on to raise $500,000 from its participation in Y Combinator’s (YC) winter ’23 program, and it recently made its first engineering hire who joined them from enterprise software giant Red hat.
Aside from lead backer Gradient Ventures, the company’s seed round included investments from YC, 22 Ventures, and angel backers such as Elad Gil and YC’s Diana Hu.


