iLeakage Vulnerability Found In Apple Silicon Can Leak Passwords To Attackers
A new vulnerability has been discovered in Apple’s A-series and M-series chips that attackers can potentially use to obtain passwords and sensitive information from iPhones, iPads, and Macs.
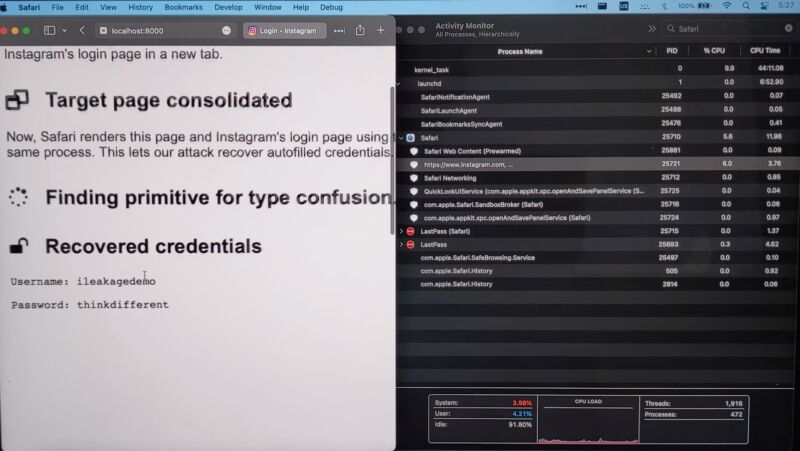
The vulnerability dubbed ‘iLeakage’ affects any browser on an iOS device and Safari browser on a Mac. In a proof of concept, researchers used the iLeakage vulnerability in order to access the targetted device’s passwords auto-filled by Safari, YouTube watch history, and Gmail inbox.
In the proof of concept, researchers set up the iLeakage vulnerability as a website, which was then visited from the targetted iOS device and Mac. When the website is visited, it opens another website in the background, which will then extract the user’s sensitive information from that session.
Here’s an excerpt from Arstechnica’s report explaining how iLeakage works.
The researchers implement iLeakage as a website. When visited by a vulnerable macOS or iOS device, the website uses JavaScript to surreptitiously open a separate website of the attacker’s choice and recover site content rendered in a pop-up window. The researchers have successfully leveraged iLeakage to recover YouTube viewing history, the content of a Gmail inbox—when a target is logged in—and a password as it’s being autofilled by a credential manager. Once visited, the iLeakage site requires about five minutes to profile the target machine and, on average, roughly another 30 seconds to extract a 512-bit secret, such as a 64-character string.
– Arstechnica
The iLeakage vulnerability of Apple’s chip is a variant of the Spectre and Meltdown chip flaws discovered in 2018. While Apple has added protections in its chips to make them secure against those vulnerabilities, the new iLeakage vulnerability overcomes those protections.
When it comes to using iLeakage to extract user’s sensitive information, the attacker will need to pull out a highly sophisticated attack that requires a high caliber of technical expertise. This means this is not an attack your everyday attacker could pull off. The researchers also point out that it is very unlikely that this vulnerability is known to attackers and is not being actively exploited in the wild.
Now it is up to Apple to close this vulnerability and make its chips secure before this exploit is used by attackers.
(via 9to5Mac)


